The Tornado Cash indictment was only the latest salvo in the ongoing “crypto wars.”
In an astounding move, the U.S Department of the Treasury’s FinCEN agency has issued a new proposal that seeks to broadly expand the terrorist financing restrictions in the PATRIOT Act to cryptocurrencies. This extension would have all cryptocurrency privacy tools, regardless of technical function, custody, or decentralization be considered a threat to national security, and thus subject to extensive reporting to FinCEN by all regulated entities. This reporting would lead to a centralized and comprehensive list of all users of privacy tools, making further crackdowns and legal action against those seeking privacy much easier in the future.
This proposal is the latest in a long line of aggressive and expansive efforts by the U.S. government to collect information, collate it, and often prosecute anyone seeking to provide or use privacy tools when using cryptocurrencies, and will further limit the ability of individuals world-wide from gaining access to necessary financial privacy in the cryptocurrency economy.
The Supposed Justification
To propose a broad and sweeping set of additional regulations, FinCEN must set forth clear reasons before the broader government and populace for why this new regulation is supposedly necessary. In the aftermath of the outbreak of conflict in the Middle East, FinCEN has shifted their “boogeyman” from North Korean hackers to focus more heavily on Hamas and ISIS. Wielding a security risk that is a pressing topic in the mainstream media is an age-old tactic of the U.S. government, and while it’s clear this proposal was in the works long before the conflict in the Middle East broke out, they’re attempting to use it to provide “teeth” for this proposal.
There seems to be very little evidence to support these claims, however, with even Chainalysis denouncing much of the attribution of cryptocurrency usage to Hamas and other terrorist organizations as grossly exaggerated due to inaccurate chain surveillance, saying that they “have also seen overstated metrics and flawed analyses of these terrorist groups’ use of cryptocurrency.” But let’s take a look at the specific claims made by FinCEN in the proposal around justification ourselves.
Criminals like privacy, shockingly
While the claims made in the proposal are that illicit actors are heavy users of privacy tools, FinCEN makes no explicit claim on how much funding Hamas has received through cryptocurrency, much less how much (if any) of their funding flowed through privacy tools. Instead, they leverage their previous prosecutions of privacy tool admins and developers to attempt to show that criminals like privacy (shocker):
The multiple U.S. Government actions against CVC mixers… demonstrate that CVC mixing provides illicit actors with enhanced anonymity in CVC transactions, allowing them to more easily launder their illicit proceeds in CVC.
The cases referenced here in the proposal are those of Helix and Tornado Cash, both of which were cases against the operators of privacy tools, instead of any effort to go after the illicit users themselves. In the case of Helix, the government was only able to show that ~12% of deposits into Helix were from illicit sources, even though they captured the entire mixing infrastructure and had full access to all mixing wallets and transaction history. In the case of Tornado Cash, the government was only able to attribute ~7% of inflows to illicit sources despite all inflows on the Ethereum network being transparent by default and almost always trivial to trace to their origination point.
Illicit usage increasing, or legitimate users being scared off?
One of the other commonly cited justifying statistics throughout the proposal is that of illicit usage supposedly increasing over the past few years in the cryptocurrency space. To support these claims, FinCEN relies almost exclusively on Chainalysis’ reporting, and yet exclude the possibility of their fear tactics having an outsized impact on legitimate usage of privacy tools.
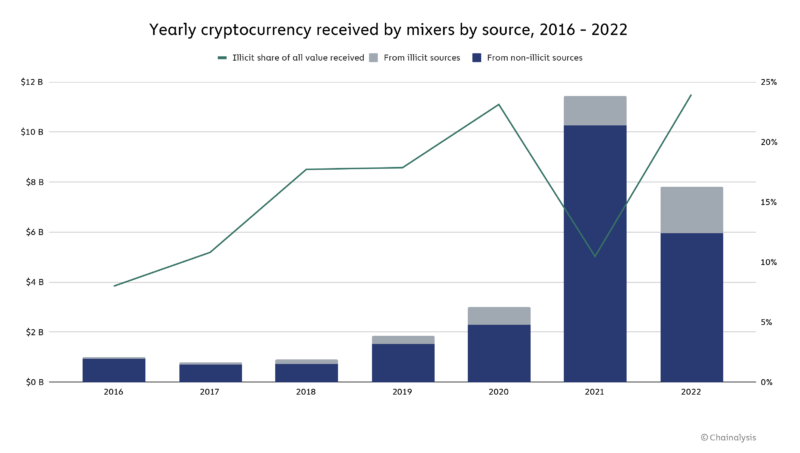
However, the analysis noted the CVC that was sent to CVC mixers in 2022 was more likely to come from illicit sources than in previous years—24 percent of the $7.8 billion processed by mixers in 2022 versus 10 percent of the $11.5 billion processed by mixers in 2021.
While on its face this seems like a serious increase in illicit usage as a share of total usage, you have to fully consider what happened in 2022. In August, the DOJ issued sanctions against the entirety of the Tornado Cash project, signaling to the cryptocurrency world that even legitimate usage of privacy tools could be considered illegal overnight. In addition to that, the DOJ also prosecuted several other privacy tools, including the aforementioned Helix. These two cases were used as weapons of fear against both illicit and licit users alike, and led to a significant drop-off in total usage of privacy tools in the space. Even Chainalysis themselves makes the same conclusion in their report, stating that “[t]he data suggests that legitimate users have decreased their use of cryptocurrency mixers” as a result of these actions.
Can we trust Chainalysis’ numbers?
These claims all rely on Chainalysis’ surveillance software being provably accurate and effective, something that we learned even Chainalysis’ own head of investigations doesn’t claim in a recent article on Bitcoin Magazine by L0la L33tz. L0la has spent the past few months digging through court documents and interviews to pull back the veil on the cooperation and dealings between the U.S. government and Chainalysis, so I reached out to her for comments on this proposal. She made it clear that we should be wary of their methods, as:
…the majority of heuristics and clustering algorithms applied have no scientific basis. Blockchain surveillance has no KPIs. The methodologies provided to inform FinCEN’s guidance have not been independently verified, leaving them subject to biases, faulty calculations, and wrong assumptions. FinCEN cannot, beyond a reasonable doubt, exclude the possibility that the Treasury has been misled or misinformed in its entirety by private corporations braving substantial conflicts of interest.
L0la’s comments are insightful and pointed; using a piece of black box software run by a company that stands to make immense profits if this proposal passes leads to all kinds of broken incentives and conflicts of interest. While Chainalysis will of course claim that their numbers are valid, even competitors in the chain surveillance space have made it clear that their work is “more art than science” in a marketing blog post. When both the government and their contracted agent in Chainalysis stand to gain power and wealth through this proposal, we should be very wary of trusting their black-box figures.
For more on the topic of Chainalysis and their recent battle to keep their proprietary methods secret, you can dive into some of L0la’s other articles along with a podcast below:
- Chainalysis, the Theranos of blockchain forensics? | Bitcoin Magazine
- Chainalysis denounces Bitcoin Core contributor as "unqualified" | Bitcoin Magazine
- US government frames Bitcoin privacy as "criminal" | Bitcoin Magazine
- Is Chainalysis Prosecuting Innocent People with L0la L33tz | What Bitcoin Did
What counts as a “mixer?”
Before the sanctions and subsequent indictment against Tornado Cash, the previous understanding of what counted as a “mixer” and “money transmitter” under FinCEN guidance was thought to be limited to only those services that take custody of funds and have a centralized business behind them. Unfortunately, the U.S. government has taken leaps to expand that definition over the past 18 months, leading to the proposal at hand.
The term “CVC mixer” means any person, group, service, code, tool, or function that facilitates CVC mixing. FinCEN acknowledges this definition is relatively broad; however, given the nature of CVC mixing, FinCEN deems the breadth of this definition to be necessary.
FinCEN held back no punches here, deeming anything and everything that could provide a shred of privacy to be categorized as a “mixer” under the new set of rules. To further clarify their definition, they expand on the act of “mixing” below (emphasis mine):
The term “CVC mixing” means the facilitation of CVC transactions in a manner that obfuscates the source, destination, or amount involved in one or more transactions, regardless of the type of protocol or service used.
While FinCEN outlines six specific categories of tools as a mixer, they are clear that these are just example categories and are not an exhaustive list. These categories are:
- “Pooling or aggregating CVC from multiple persons, wallets, addresses, or accounts”
- “Splitting CVC for transmittal and transmitting the CVC through a series of independent transactions”
- “Using programmatic or algorithmic code to coordinate, manage, or manipulate the structure of a transaction”
- “Creating and using single-use wallets, addresses, or accounts and sending CVC through these wallets, addresses, or accounts in a series of transactions”
- “Exchanging between types of CVC, or other digital assets”
- “Facilitating user-initiated delays in transactional activity”
These categories would seemingly include every cryptocurrency privacy tool (and many non-private tools, incidentally) currently in existence, including (but definitely not limited to):
- Centralized mixing services (i.e. Helix)
- Centralized Coinjoin tools (i.e. Wasabi Wallet)
- Decentralized Coinjoin tools (i.e. Joinmarket and Payjoins)
- Centralized “instant exchangers” (i.e. FixedFloat)
- Decentralized privacy tools (i.e. Tornado Cash)
- Decentralized privacy coins (i.e. Monero)
- Decentralized exchanges used to swap between cryptocurrencies (i.e. Bisq)
Any tool or service that prevents trivial tracking of the flow of funds on-chain falls under this category, and thus any usage of these tools would count as “mixing” under this new compliance regime. FinCEN fully understands that this scope is incredibly broad and encompasses many tools normally outside of the scope of privacy tools, and yet seems to not care at all. L0la L33tz, author of the aforementioned article on Chainalysis methods, added in her comments that this flagging of regular individuals seeking privacy as high risk arbitrarily assumes guilt. She goes on to add that “[t]he attempt to hold a group of people responsible for the unlawful actions of individuals, as suggested in FinCEN‘s proposal, is deemed collective punishment and illegal under international law.”
What this means for regulated entities
The immediate impact of this proposal would be increased reporting for regulated entities like cryptocurrency exchanges, requiring them to not only collect their normal KYC/AML information from customers, but also additionally provide detailed information on any user who has a history of interaction with mixers in the past. This additional reporting would then be bundled with all known KYC/AML information on any user of privacy tools and sent directly to FinCEN within 30 days. While FinCEN claims that his will not have a major impact on costs for regulated entities, it will involve drastically more expansive chain surveillance by companies like Chainalysis, increased reporting requirements, and a host of new data points to collect and collate for submission to the government.
This additional cost and effort will necessarily increase costs for the customer as exchanges and service providers must spend far more on surveiling and reporting on their customers activities.
The ineffectiveness of the compliance regime
FinCEN makes many claims about how effective this new proposal will be at dissuading and prosecuting privacy tool usage by illicit actors, and yet provide no concrete data to back their claims. When we look at the history of the compliance regime and attempt to gauge any sort of success metrics, it becomes incredibly clear that their attempts to fight illicit usage through reporting and regulation have been colossal failures that cost financial entities (and thus their customers) far more than they’re worth.
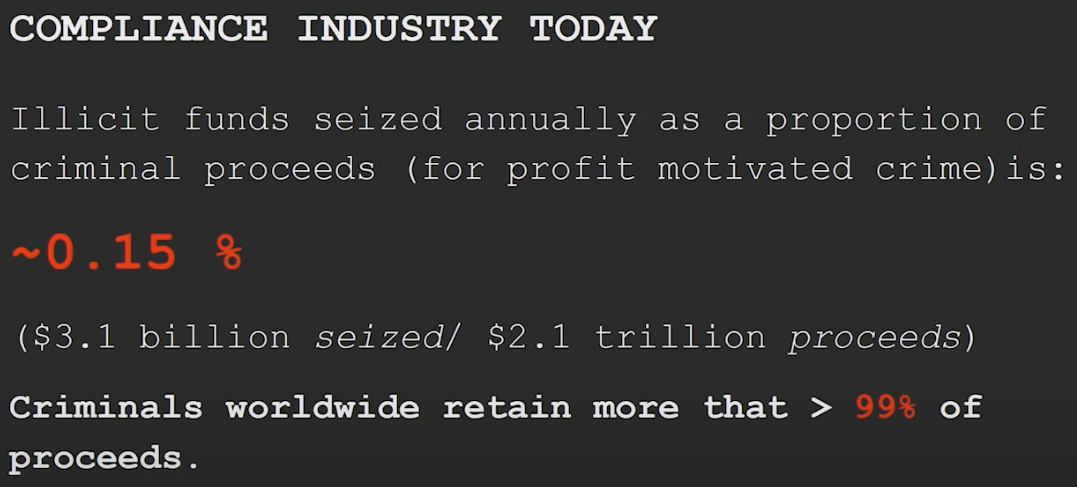
Not only is the financial loss due to compliance costs detrimental to an effectively functioning financial system, the privacy costs associated with our financial activity being surveiled, collected, and collated are hard to measure but sure to haunt us in the future. For an excellent primer on our rights to human privacy and the complete failing of the compliance regime, we recommend this talk by Silke Noa at this year’s Hacker’s Congress Paralelni Polis:
What this means for you
If you use any U.S. service providers or exchanges
This proposed regulation would mean that any time you interact with a U.S.-based regulated entity — i.e. a centralized exchange like Coinbase — they will be required to report you directly to FinCEN if there is any history of mixer usage associated with your funds. This reporting would include the standard KYC/AML data but be greatly expanded. The proposal includes an exhaustive list of information to be collected and submitted to FinCEN within 30d of mixing activity being noticed:
- The amount of any CVC transferred, in both CVC and its U.S. dollar equivalent when the transaction was initiated
- CVC type
- The CVC mixer used, if known
- CVC wallet address associated with the mixer
- CVC wallet address associated with the customer
- Transaction hash
- Date of transaction
- IP addresses and time stamps associated with the covered transaction
- Narrative
- "A summary of investigative steps taken, provide additional context of the behavior, or other such information the covered financial institution believes would aid follow on investigations of the activity."
- Normal KYC/AML information:
- Full name
- Date of birth
- Address
- Email address for all accounts
- Unique identifying number (i.e. SSN)
Any usage of mixers by FinCEN’s broad definition will get you added to a special list and all of your personal details sent off to FinCEN for tracking, making it trivial for the government to take further action to limit or prosecute any usage of privacy tools in the future.
This proposed rule would compel covered financial institutions to attribute a covered transaction to the involved customer(s) and report this information to FinCEN.
The creation of lists are always the starting point for further attacks against human rights when it comes to governments, and their clear hatred for privacy tools makes this specific list especially dangerous to be on moving forward.
If you use any international service providers or exchanges
While this proposal will initially only impact regulated entities that are subject to U.S. law, there is broad precedent for FinCEN’s proposals being rapidly adopted by other countries and ruling bodies across the globe. FinCEN sets much of the global regulation through its actions, and unfortunately much of the world quickly follows in their footsteps. Even if you are not currently subject to this proposal, that does not mean that it won’t apply to the services and exchanges you use today in the near future.
If you don’t use any service providers or exchanges
For those of you who have already opted out of the broken compliance regime and begun to use decentralized exchanges and no-KYC tools, this will have little impact on you today. It is likely that long-term usage of these tools will lead to funds being considered tainted and thus subject to this reporting if they ever enter the standard, regulated economy, but within the burgeoning Bitcoin circular economy things can go on as normal.
What this means for the cryptocurrency space
Ultimately, this is a further monumental leap in the U.S. governments attempts to prevent the usage of privacy tools in the cryptocurrency space. This crackdown, especially with the broad definitions imposed by FinCEN here, will kick-start the bifurcation of cryptocurrencies into two worlds — white-market and black-market money.
Users and entities who avoid privacy tools and decentralized exchanges will be able to continue operating within the “gilded cage” of the approved regulated entities and functional normally, albeit with much tighter surveillance and scrutiny around their on-chain activities.
Those who choose to take action and seek financial privacy through privacy tools, on the other hand, will be banished to a black-market circular economy. This economy will have to function separately from the state and traditional on- and off-ramps like centralized exchanges, as any usage of these services while leveraging privacy tools would lead to an automatic reporting of activity and personal information to a state intent on shutting down said tools.
The cryptocurrency world will split into two separate economies, one that functions as an add-on to the traditional finance and compliance regime, and one that acts as an independent and self-sustaining circular economy.
Guilty until proven innocent
This line of reasoning by FinCEN continues the steps of the U.S. government to shift the judicial system from one of “innocent until proven guilty” to a tyrranical system of “guilty until proven innocent," according to L0la. This shift has been seen in the case against Tornado Cash and even in subsequent efforts by the Ethereum community to bend to regulators. FinCEN’s chosen approach would have any attempt to seek privacy by the average individual have them thrown into the same suspicions as terrorists and dictators, making the words of Phil Zimmerman ring more true than ever:
If privacy is outlawed, only outlaws will have privacy.
What we can do
Be optimistic
As we laid out in our article on the Tornado Cash indictment, the drastic steps governments are taking to prevent the usage of privacy tools in the cryptocurrency space shows that they feel threatened:
It may not be immediately apparent, but one of the biggest takeaways is quite simple – we're winning. The fact that a massive government like the U.S. feels threatened enough by privacy tools to take overt legal action shows that the powerful tools being built out to empower you, the user, are working. The immense uptake of privacy tools like Signal, Proton Mail, and the Tor network have started to shift the balance of power back towards the individual.
The more push-back and fight we see from governments across the globe against encryption and privacy-preserving tools, the more evidence we have that the tools are actually working.
In addition, we can be optimistic because this is still just a proposal as of publishing. It is possible that this proposal will be shot down through mass sentiment and outcry. We are hopeful that will be the case and will do all we can to help prevent this proposal from being accepted as-is.
Keep using privacy tools
The last thing we want for our readers is that you should give in and stop using privacy tools today. There are excellent tools out there in the space that you can leverage to gain on-chain privacy, and we must continue to use them to gain the full measure of freedom that freedom money like Bitcoin can provide. Tools that allow you to reclaim your financial privacy like Samourai Wallet (a powerful, privacy-preserving wallet for Bitcoin) and Monero (a cryptocurrency that protects sender, receiver, and amount in every transaction) are indispensable tools for freedom, and should be something you practice with regularly, no matter what the state says.
If we allow regulation and fear tactics to dissuade us from fighting for the right to privacy, our ability to transact without fear of surveillance or censorship will be slowly stripped away from us.
Opt out of KYC exchanges covered by this guidance
The most practical advice we can give here is to opt out of the broken compliance regime entirely. The crux of FinCEN’s proposal hinges on centralized exchanges with broad swaths of user data complying, and most of these regulated entities will happily go along if profits continue. Thankfully, there are excellent solutions out there for getting into (and out of) cryptocurrency without being subject to heinous over-regulation and surveillance. These solutions make it so that you can continue using privacy tools to protect your right to financial privacy without being cut-off from the traditional economy.
If you want to learn more about where to get started with joining the “no-KYC” movement, you can find some excellent resources below:


Let your voice be heard
A key way that you can support the push against this proposal is to support it publicly. Sharing posts like ours within your sphere of influence (friends, family, social media following, etc.) can help to shift public sentiment away from invasive and abusive proposals like this one and make it more difficult and costly for FinCEN to enact this or similar regulation.
Join the Conversation
If this post has sparked an idea or motivated you to get involved, there is no better next step then to join the conversation here at freedom.tech! Subscribers can jump straight into the comments below, or you can join our community SimpleX or Signal groups:

If you have feedback for this post, have something you'd like to write about on freedom.tech, or simply want to get in touch, you can find all of our contact info here:











